The attack bears the hallmarks of ransomware but a spokesperson at the Vestas refused to be drawn on the specific nature of the attack at this stage. Targeted attacks manually executed by criminal organizations and more sophisticated threat actors that typically follow the attack lifecycle and often leverage trusted applications that live in the customer environment to reduce risk of detection ie.
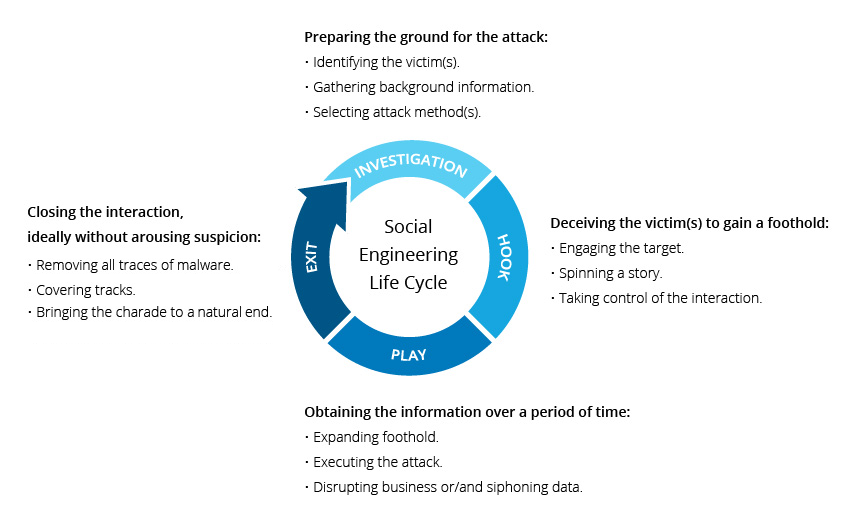
What Is Social Engineering Attack Techniques Prevention Methods Imperva
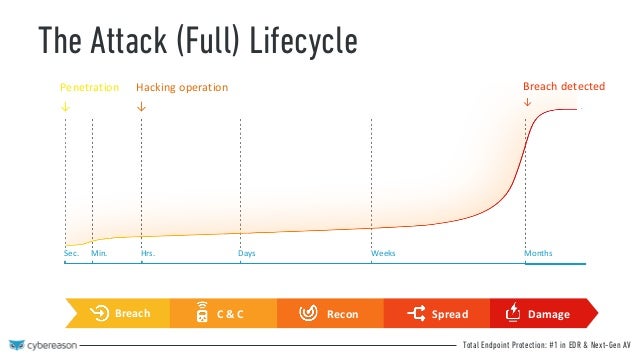
The Cyber Attack Lifecycle
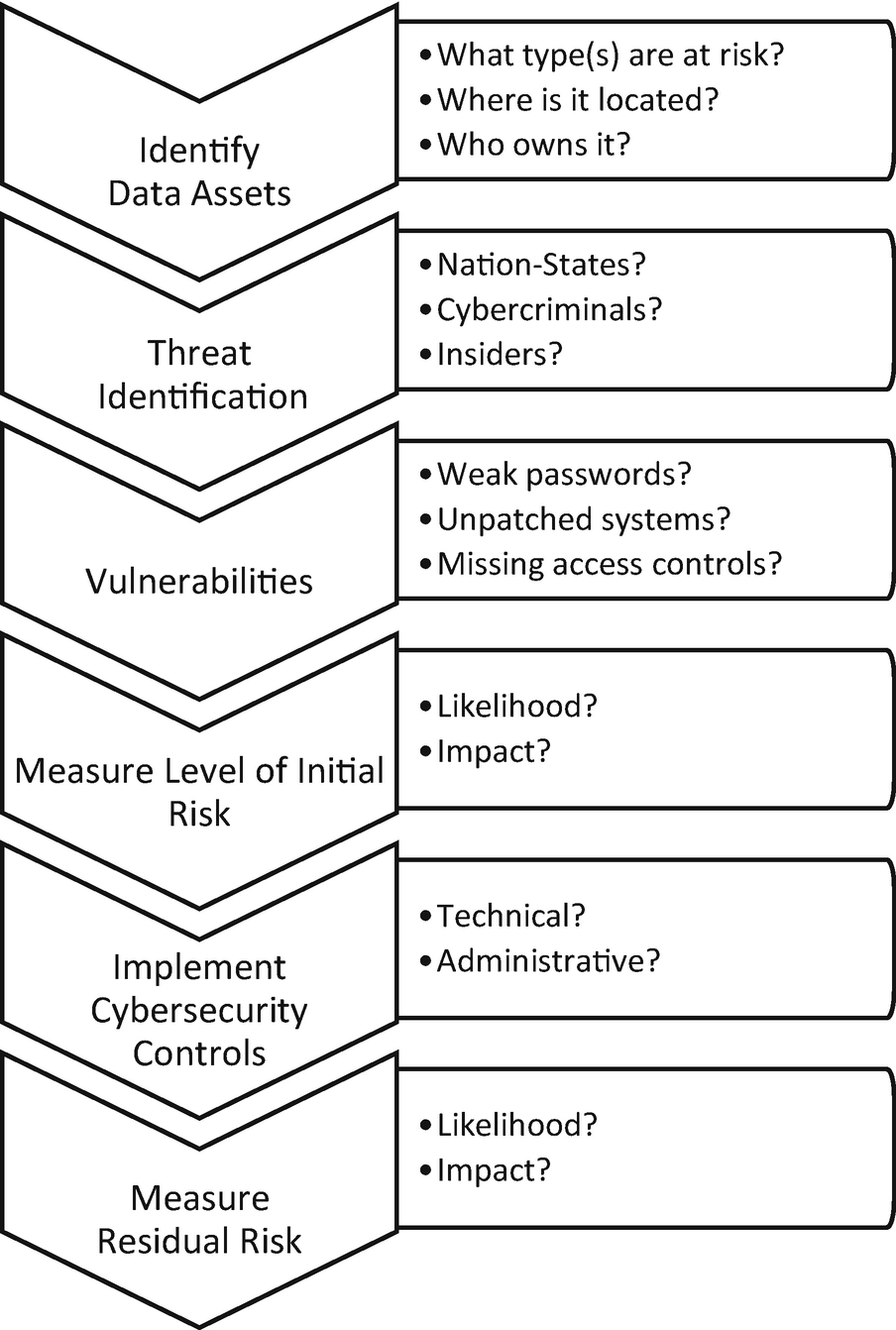
Cyber Risks And The Attack Life Cycle Springerlink
If you dont have a strong foundation of end-to-end security and full lifecycle protection youre not going to have any privacy.

Cyber attack lifecycle. IT security standards or cyber security standards are techniques generally set forth in published materials that attempt to protect the cyber environment of a user or organization. 1 Advanced Persistent Threats. This environment includes users themselves networks devices all software processes information in storage or transit applications services and systems that can be connected directly or indirectly to networks.
Insurance products and services offered by Aon Risk Insurance Services West Inc Aon Risk Services Central Inc Aon Risk Services Northeast Inc Aon Risk Services Southwest Inc and Aon. Main Cyber Security Challenges. Cyberbit enables information security leaders to manage their teams entire skill development lifecycle in one SaaS platform.
They are designed specially to mine highly sensitive information and these days many organizations. Cyber Threat Detection and Response Solutions. Contain and recover from cyberattacks with Kivus forensics-forward rapid-response service built with cyber insurability in mind.
Critical infrastructure and information. Axellio provides economic end-to-end cyber security solutions designed for your team environment and security objectives providing packet level visibility across your network. Following are some cybersecurity challenges explained in detail.
Forces to maneuver in the cyber domain while denying the adversarys ability to do the same and simultaneously protecting US. Cyber Defense Labs helped this global law firm enhance and update Business Continuity Plans and Information Technology Disaster Recovery Plans. Software supply chain attacks on the rise.
Indiscriminate attacks that leverage a self-propagation or worm-like capability to continually redeploy malware. One of the key priorities is to keep stakeholders well informed without releasing information that could compromise the handling of the situation he told The Register refusing to confirm or deny whether a ransom was under demand. The result is a far more rich and nuanced understanding of intrusion analysis and this approach has formed the basis for most of the intrusion detection and SIEM tools that exist today.
The motivation is to fill the knowledge gap by presenting some of the ways of data leakages and the likely protection in the organization. The NCSC is seeking companies to help develop the assurance scheme for new Cyber Incident Response and Cyber Incident Exercising Services. November 18 2021 Microsoft named a Leader in IDC MarketScape for Modern Endpoint Security for Enterprise and Small and Midsize Businesses The security stakes have never been higher and consequently the protection of endpoints as a key component of any extended detection and response strategy has never been more criticalfor organizations of all sizes.
Cisco Cyber Vision allows IT and OT teams build a common understanding of their industrial security posture so they can work together on reducing the attack surface. From responding to and containing active attacks to post-incident analysis with world. 80 of senior cybersecurity leaders see ransomware as a dangerous growing threat that is threatening our public safety.
Advanced persistent threats go the stealthy way around to penetrate systems and servers and stay there for a longer time without getting noticeddetected by anybody. Three Types of Ransomware. Similarly the average lifecycle of a data breach in the healthcare sector is 329 days whereas the overall average is 280 days.
Screen candidates onboard new hires quantify your teams capabilities plan your skills development program run live-fire cyber range exercises and identify gaps to ensure your team is ready to respond to the most recent threats. The new normal landscape has generated a surge of sophisticated Gen V cyber attacks including targeted ransomware. Indicators of Compromise IOCs are the evidence such as URLs IP addresses system logs and malware files that can be used to detect future breach attempts using intrusion detection systems IDS and antivirus.
The aim is to present a good practice that encourages data. Our cyber efforts involve a close coupling of computer network defense computer network attack and exploitation computer network development and engineering. Cyber security services offered by Stroz Friedberg Inc.
This paper review seeks to identify the need for a revamped data life cycle security in the era of pervasive threat from skill cyber criminals at this time of internet of things. The attack graph allows the cybersecurity analyst to identify not only each step of the Cyber Kill Chain but also individual pivot points the hacker takes within those steps. Our work helped ensure the safety of trusted client and employee data which the firm considered a top priority that was critical to their business operations.
Protecting Against a Rapidly Spreading Cyber Pandemic. With the Covid-19 outbreak cyber criminals have seized this global crisis to launch treacherous cyber exploits. The cyber kill chain identified the phases of a cyber attack from early reconnaissance to the goal of data exfiltration and used as a tool to improve an organizations security.
So here are some industry-specific cyber attack statistics to give you an idea about the current state of cybercrimes in each sector. Cavoukian on Newfoundland cyber attack. Combined with Cisco ISA3000 industrial firewall Cisco ISE and SecureX Cyber Vision offers unique network segmentation threat detection and remediation capabilities to ensure continuity and safety of your.
The Cyber Pandemic is here. Over the 202021 financial year the ACSC received over 67500 cybercrime reports an increase of nearly 13 per cent from the previous financial year. The increase in volume of cybercrime reporting equates to one report of a cyber attack every 8 minutes compared to.
Ensuring that the full incident lifecycle is covered from initial discovery through to close down. OneLogin Workflows is a powerful way to automate more complex identity lifecycle management use cases like custom provisioning time-based actions and custom notifications. Here are six principles to improve the cybersecurity of critical infrastructure.
The recent cyber-attack on the US major oil and gas pipeline could become one of the most expensive attacks to an economy. In software supply chain attacks the threat actor typically installs malicious code into legitimate software by modifying and infecting. At a high level the threat intelligence lifecycle outlines the core steps to apply and uphold high standards of data hygiene necessary to confidently draw conclusions and take action based on the data.
The threat intelligence lifecycle is a fundamental framework for all fraud physical and cybersecurity programswhether mature and sophisticated in their operations or merely aspiring. Were with you throughout the attack lifecycle. In its mid-year report Check Point Research provides analysis of the year to date looking at global cyber attack trends in malware overall ransomware and mobile and cloud malware.
The Islamic Republic says it remains on alert blaming the United States and Western powers for such strikes in the pastThe post Iran claims cyber attack caused major damage to.

Cybersecurity Lifecycle

Cyber Kill Chain Explained Steps And Drawbacks
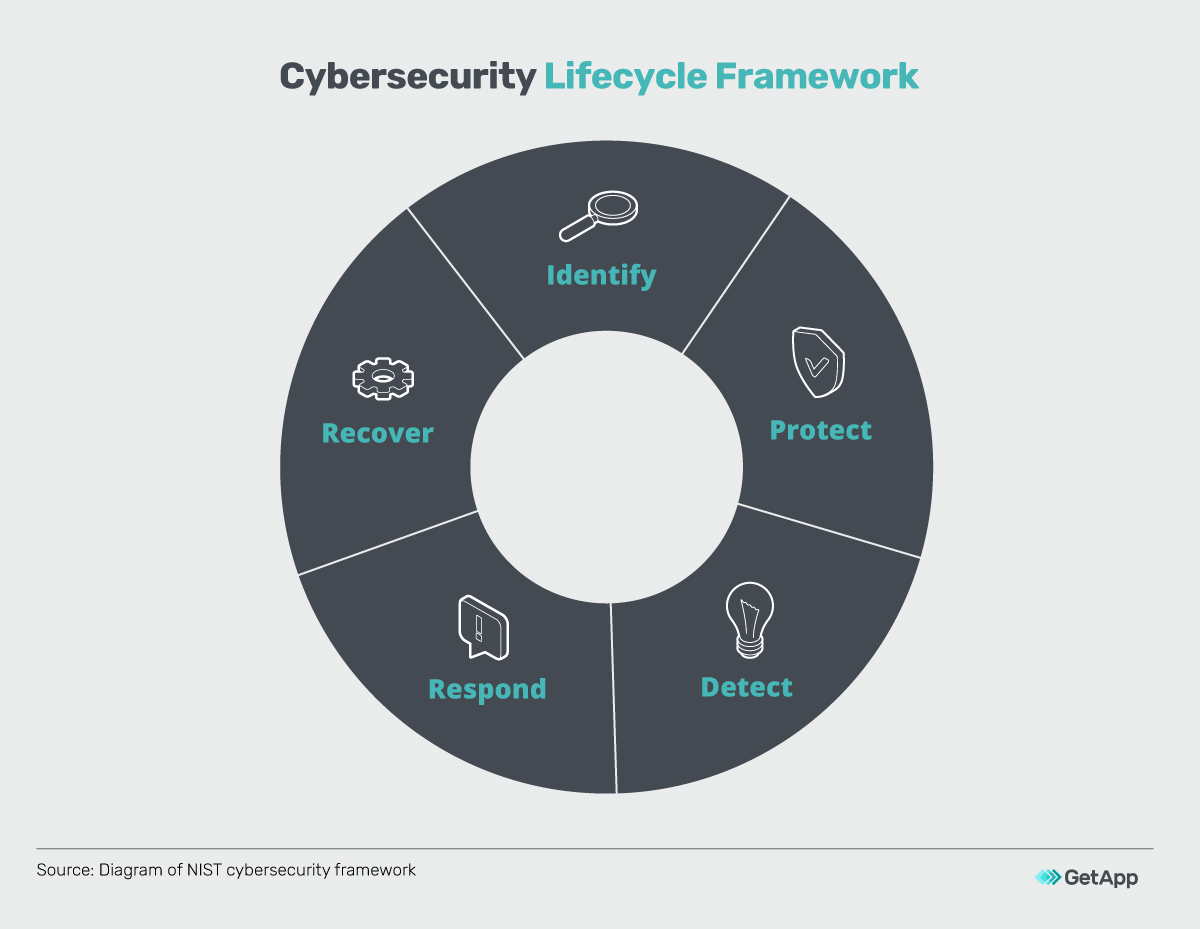
Building A 5 Phase Cybersecurity Lifecycle Framework For Your Business

The Tyler Cybersecurity Lifecycle
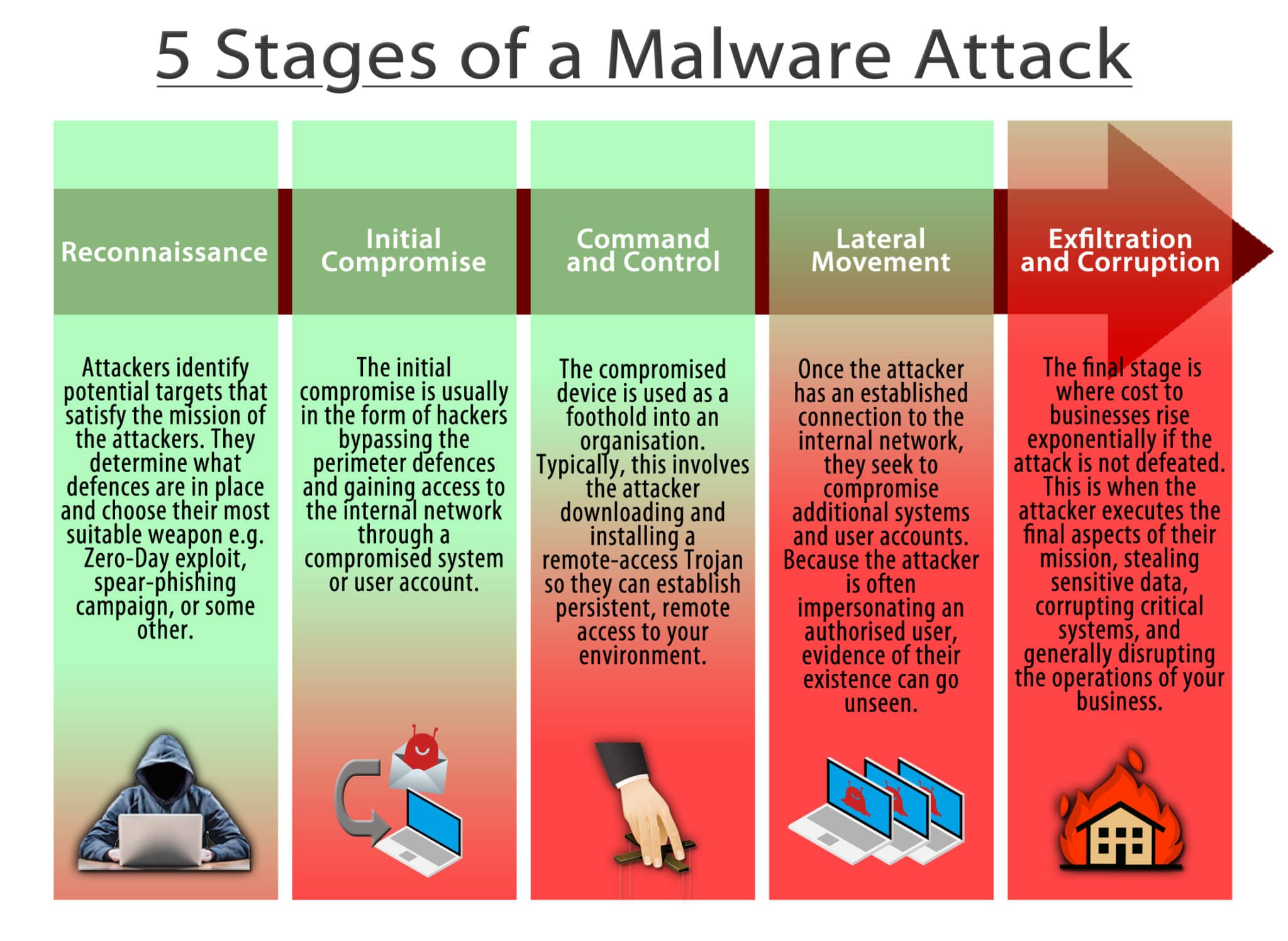
5 Stages Of A Malware Attack Cyber Security Tesrex

The Lifecycle To Manufacturing Cybersecurity Resilience Sentis

The Cyber Attack Lifecycle Youtube

The Attack Life Cycle
